Switching and VLANs
Switching is a core component of networking, responsible for connecting devices within a network and efficiently forwarding data frames based on MAC addresses. VLANs (Virtual Local Area Networks) build upon switching to logically segment networks, improving performance, security, and manageability.
What is Switching?
Switches operate at Layer 2 of the OSI model, forwarding Ethernet frames based on MAC addresses. They maintain a MAC address table, mapping MAC addresses to specific switch ports, which allows them to send traffic only to the intended recipient instead of broadcasting it to all connected devices.
Types of Switching
- Cut-Through: Forwards frames as soon as the destination MAC address is read, offering low latency but risking corrupted frame forwarding.
- Store-and-Forward: The switch stores the entire frame, checks for errors, and then forwards it. This method is more reliable but has slightly higher latency.
- Fragment-Free: A compromise between the two, forwarding frames after reading the first 64 bytes (where most errors occur).
What are VLANs?
A VLAN (Virtual Local Area Network) is a logical grouping of devices in a network, regardless of their physical location. VLANs segment a network into isolated sections, allowing devices in one VLAN to communicate only with others in the same VLAN unless explicitly permitted through routing.
Let's take a look at what a network would look like without VLANs.
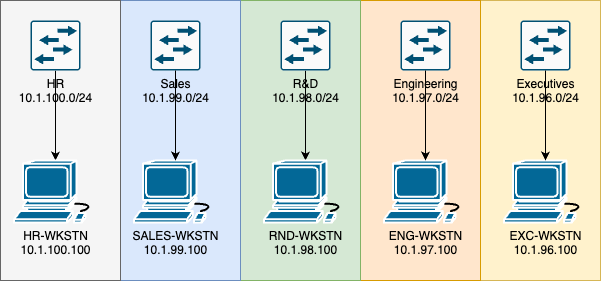
What we have here are 5 different, logical and physical networks. The HR workstation cannot talk to the executive workstation, R&D cannot talk to Engineering, etc. Everyone is on their own island. While this might be the intended results, it would be expensive. If this was a single office, the switch closet would need to have 5 physical switches. We'd also need a router with 5 physical interfaces. This also equates to cost. Now imagine trying to manage 5 different networks. You have to stage 5 sets of updates, troubleshooting would take longer, etc.
So how can we make this more affordable and easier to manage without compromising our intended results? VLANs! Lets take a look at our network with VLANs.
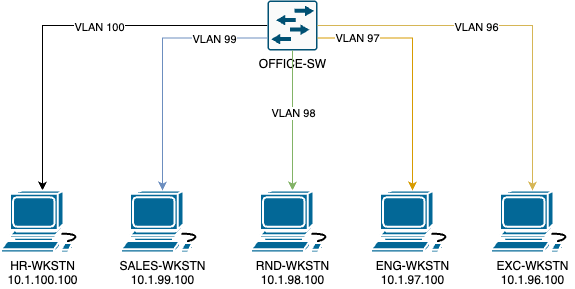
Now we have a single office switch and each workstation is now connected to a respective VLAN. Even in this configuration, the workstations cannot talk to each other directly as there is no router. But you can see that there are 5 independent networks on a single switch. See how great VLANs are?
Benefits of VLANs
- Improved Security: Sensitive data can be isolated from the rest of the network.
- Better Performance: Reduces broadcast traffic by limiting it to specific VLANs.
- Enhanced Manageability: Logical segmentation simplifies network changes and expansions.
- Flexibility: Devices can be grouped based on function, department, or location, irrespective of their physical connections.
Configuring VLANs
Here’s an example of VLAN configuration on a Cisco switch:
# Create VLANs Switch(config)# vlan 10 Switch(config-vlan)# name Accounting Switch(config)# vlan 20 Switch(config-vlan)# name Sales # Assign ports to VLANs Switch(config)# interface FastEthernet0/1 Switch(config-if)# switchport mode access Switch(config-if)# switchport access vlan 10 Switch(config)# interface FastEthernet0/2 Switch(config-if)# switchport mode access Switch(config-if)# switchport access vlan 20 # Configure a trunk port Switch(config)# interface GigabitEthernet0/1 Switch(config-if)# switchport mode trunk Switch(config-if)# switchport trunk allowed vlan 10,20
In this example:
- VLAN 10: For the Accounting department.
- VLAN 20: For the Sales department.
- Trunk Port: GigabitEthernet0/1 is configured as a trunk to allow traffic for VLANs 10 and 20 to pass between switches.
Trunking and VLAN Tagging
Trunking allows multiple VLANs to be carried over a single link between switches. VLAN tagging uses the IEEE 802.1Q standard to add a VLAN ID to each Ethernet frame, ensuring that frames are correctly forwarded to their respective VLANs.
Key Trunking Concepts
- Native VLAN: Untagged frames on a trunk are associated with the native VLAN.
- Allowed VLANs: Specify which VLANs are permitted on a trunk link to restrict unnecessary traffic.
Inter-VLAN Routing
While VLANs isolate traffic, devices in different VLANs often need to communicate. Inter-VLAN routing is used to route traffic between VLANs, typically achieved through a Layer 3 device like a router or Layer 3 switch.
Here’s an example of inter-VLAN routing configuration on a Layer 3 switch:
# Enable routing Switch(config)# ip routing # Create VLAN interfaces Switch(config)# interface vlan 10 Switch(config-if)# ip address 192.168.10.1 255.255.255.0 Switch(config)# interface vlan 20 Switch(config-if)# ip address 192.168.20.1 255.255.255.0
Best Practices for VLANs
- Use a VLAN Design Plan: Clearly define VLANs for departments, functions, or security zones.
- Minimize Broadcast Domains: Avoid excessively large VLANs to reduce broadcast traffic.
- Secure the Native VLAN: Change the default VLAN ID (1) to reduce security risks.
- Document VLAN Assignments: Keep track of VLAN IDs and their purposes to simplify troubleshooting and management.
Advanced VLAN Topics
Once you’re comfortable with the basics, explore these advanced VLAN concepts:
- Private VLANs: Further segment a VLAN to isolate specific ports for security or performance.
- Dynamic VLANs: Use a VLAN Management Policy Server (VMPS) to dynamically assign VLANs based on MAC addresses.
- Voice VLANs: Separate voice traffic from data traffic for better QoS in VoIP deployments.
Tools for Learning Switching and VLANs
Here are some tools to practice and explore switching and VLAN configurations:
- Cisco Packet Tracer: Simulate Cisco network devices and configurations.
- GNS3: Advanced network simulation platform for virtualized labs.
- EVE-NG: Create complex lab environments with virtual and physical network devices.
Common Troubleshooting Tips
If VLANs or switches aren’t working as expected, try these steps:
- Check VLAN Membership: Verify that ports are assigned to the correct VLAN.
- Validate Trunking: Ensure trunk ports are correctly configured and allowed VLANs are properly set.
- Test Connectivity: Use
pingto test connectivity between VLAN interfaces or devices. - Review Spanning Tree: Ensure spanning tree is correctly configured to avoid loops.
Switching and VLANs are foundational concepts in networking. By mastering these, you’ll be equipped to design and manage scalable, efficient, and secure networks for any environment.
